Welcome to the first blog in a series of blogs discussing phishing and social engineering – and ways of protecting yourself from hackers. We will be discussing the elements behind how hackers are trying to exploit you, and we will be discussing the techniques and other preventative controls you can take to protect yourself. In today’s blog, we’ll be discussing and describing what phishing is.
Bullet Point Summary
- Social Engineering is the art of manipulating people so they give up confidential information.
- Phishing is using email to do social engineering.
- Clicking a link could take you to a page with malware, or an illegitimate website asking for personal or confidential information.
- Downloading an attachment can also be harmful – attachments can contain malware.
- Hackers use phishing because it’s easy, simple and effect. Phishing is dangerous for these reasons also.
The News
Hardly a day goes by where you don’t see a security breach headlining in the news. From Target to the Democratic National Committee email hacks, we can’t afford to ignore the risks any longer. Whether you’re a consumer or a corporate account customer with capabilities to transmit wire transfer information or ACH files via business Internet banking, we’re all at risk with normal bank or teller operations now being done by you. Hackers know this, and instead of targeting banks directly, they are now focused in on targeting you, in the hopes that your security measures and controls aren’t sufficient.
Social Engineering
Social engineering is the art of manipulating people so they give up confidential information.
The types of information these criminals are seeking can vary, but when individuals are targeted the criminals are usually trying to trick you into giving them your passwords or bank information, or access your computer to secretly install malicious software–that will give them access to your passwords and bank information as well as giving them control over your computer.
At its most basic level, a hacker can simply ask you what your username and password are. And at it’s most simple level, we all know we would probably say no.
But, if the hacker can induce some type of urgency or provide a reason for what they need that information, then statistics and experience show that you will be more likely to provide that information.
What is phishing?
Phishing is one of the easiest and most common methods of social engineering.
It’s hacking you through your email. Specifically, it’s the practice of sending emails appearing to be from reputable sources with the goal of influencing or gaining personal information.
- Could be an attachment loading malware (malicious software) onto your computer.
- Could be a link to an illegitimate website.
Below is a sample phishing attack:
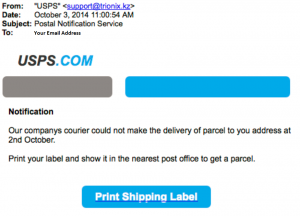
Notice who this email is from, “support@trionix.kz” is clearly not a valid USPS email address. In upcoming blogs, we’ll discuss analyzing emails and the basic underlying emotions that hackers use to get you to click links or download attachments.
What can happen if I click a link?
Clicking a link could take you to a page with malware, or an illegitimate website asking for personal or confidential information.
The act of clicking a link, depending on the malware contained in the page you’re navigating to, could potentially allow a hacker complete direct control of your computer and network.
Hackers will also redirect you to websites requesting personal or confidential information.
What can happen if I download an attachment?
The same thing as clicking a link can happen with an attachment, except that it allows the hacker immediate and direct access to your computer or network. Ransomware is an attack that is especially rampant and mostly achieved by downloading an attachment (we will talk about this in a separate blog).
Why phishing?
Phishing is a heavily successful method of compromising a person’s computer or a company’s network for the following 3 reasons.
- It’s easy
- It’s simple
- It’s effective
And for these 3 reasons, it’s the most dangerous form of social engineering.
Author
This article was written by Kaushal Kothari, President of Secure Guard Consulting, LLC, a cybersecurity / IT audit and consulting company. Kaushal is a former FDIC IT examination analyst and certified ethical hacker with 15+ years of experience in the technology field.
