Welcome to the sixth blog in our series of blogs discussing phishing and social engineering – and ways of protecting yourself from hackers. Today, we’ll be summarizing what we’ve learned about phishing.
Bullet Point Summary
- Social Engineering is the art of manipulating people so they give up confidential information; phishing is using email to do social engineering.
- Clicking a link could take you to a page with malware, or an illegitimate website asking for personal or confidential information; downloading an attachment can also be harmful – attachments can contain malware.
- In general, there are two types of phishing attacks: emotion based and authority attacks.
- Hackers will try to use emotion (urgency, panic, greed, curiosity, fear, empathy, sadness, etc.) to reduce your ability to think critically; emotion will reduce your ability to think critically and cause mistakes.
- Don’t click the link if you experience emotion from an email, and we recommend deleting any email that generates emotion.
- Spear phishing is when a fraudulent email is sent appearing to be legitimately sent by the person (for example, an attacker sending an email to you from my email address, kkothari@sgcsecure.com). This is an example of spear phishing.
- When in doubt, verify, either in person or by calling the person who may or may not have sent you an email.
Recap
In the past 5 blogs, we’ve went through phishing very in-depth. In this blog, we’re going to summarize what we’ve learned so far.
Phishing is by far the biggest cyber threat every community bank and organization faces. To protect yourself, it’s vital that you understand why these attacks are so successful.
What is Social Engineering?
Social engineering is the art of manipulating people so they give up confidential information. Take the title of this article – if I asked you for your password, would you give it to me? Probably not. But, what if I gave you a reason why should give me your password, or if I create some type of urgency, then statistics and experience show that you will be more likely to provide that information in the absence of proper training.
What is phishing?
Phishing is social engineering by email; it’s the practice of sending emails appearing to be from reputable sources with the goal of influencing or gaining personal information. Attacks are generally:
- an attachment loading malware (malicious software) onto your computer.
- a link to an illegitimate website.
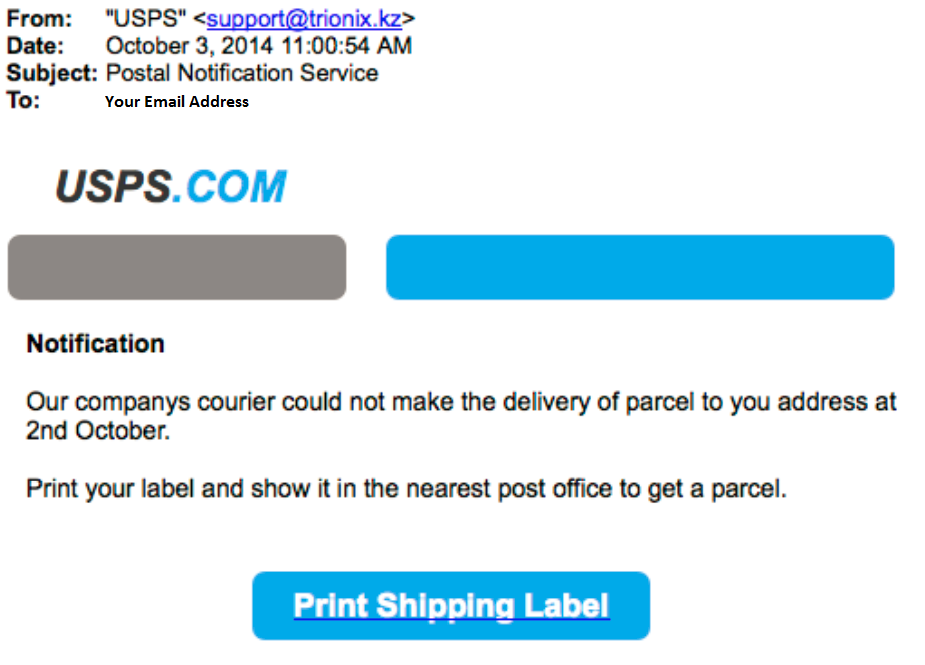
Below is a sample phishing attack. Notice who this email is from, “support@trionix.kz” is clearly not a valid USPS email address.
What can happen if I click a link or download an attachment?
Clicking a link could take you to a page with malware, or an illegitimate website asking for personal or confidential information. In fact, the act of clicking a link, depending on the malware contained in the page you’re navigating to, could potentially allow a hacker complete direct control of your computer and network. Hackers will also redirect you to websites requesting personal or confidential information. The same thing as clicking a link can happen with an attachment, except that it allows the hacker immediate and direct access to your computer or network.
Analyzing Links
Knowing how to recognize good links from bad ones is important, but as we’ll show you below, emotion based attacks seek to reduce your critical thinking making it near impossible to analyze a link. Look at the following examples – which are legitimate and which are not legitimate links? Go to blog.secureguardconsulting.com and navigate to “Phishing – Are you Susceptible? (Part 3)” to see the answers and descriptions.
- http://microsoft.com/file.txt
- http://secure-microsoft.com/file.txt
- https://secure.microsoft.com/file.txt
- http://microsoft.com/secure/file.txt
- http://rnicrosoft.com/file.txt
- http://microsoft-securitycenter.com
Links and attachments are used in essentially two types of phishing attacks: emotion based and authority attacks.
Emotion Based Attacks
Emotion based attacks are based on a theory known as Amygdala Hijacking. The Amygdala is the part of the brain responsible for processing emotion. When we encounter something (in this case an email) that causes emotion, the thought is that the amygdala goes into autopilot to process this emotion.
In doing so, the amygdala requires extra processing power to process the emotion, and hijacks processing power from other parts of the brain, specifically it hijacks processing power from the critical thinking center of the brain.
Which means that an email that states your Amazon.com account has fraudulent activity, or that emails have been quarantined, or that you’ve won a Macy’s $1000 gift card, generates emotion, fear, urgency, panic, greed (getting something for free or winning something). And since you would be in an emotional state with processing power being drawn from the critical thinking center of the brain, we would no longer be thinking critically.
Emails that create emotion should be considered immediately suspicious.
Authority Attacks
Examples of authority attacks are spoofed emails and spear phishing emails. Both build credibility since they look like they come from someone you generally know.
An example of a spoofed email from me might have the From name and address look like: Kaushal Kothari <billing@invoicesite.com>. Always compare the actual email address to the name to see if they appear legitimate.
A spear phishing email is very powerful in that they literally look like they came from the person. My actual email address is kkothari@sgcsecure.com, so a spear phishing attack might come from Kaushal Kothari <kkothari@sgcsecure.com>. Even if you reply to this email, it will come to me.
When a spear phishing email comes through, ask yourself the question of “is this normal for the person to send me an email like this?. Also, understand if the timing is correct – if you get an email from this person on Mondays, but now this email is coming on Friday, then it’s suspicious. Look for differences in the patterns we know exist. Then simply pick up the phone and call the person, especially if the email is asking you to take some action. Calling a person back by phone to verify if the email was legitimate is the best method of determining whether the email is legitimate.
Combining Both
A combination of a spear phishing attack and an emotion based attack is one of the strongest attacks possible. For example, getting an email that looks like it came from your IT person that indicates that your password is about to lockout unless you click the link and enter your password to confirm. Because it looks like it came from you, it builds immediate credibility. The possibility of your account being locked out generates urgency and panic and in some cases even fear, but the point is that it creates emotion thereby reducing your ability to think critically.
What to look out for
Look out for emails that:
Create a sense of urgency, curiosity, greed, or any emotion.
- Have poor spelling and poor grammar.
- Are unexpected.
Always …
Verify the sender’s email address.
- Hover over a link to see the actual URL.
- Don’t click the link – retype to only web address you know!
And remember:
- Hackers can send emails from you to yourself, your IT person to you, or from anyone to anyone.If out of the ordinary or requesting something,
ALWAYS PICK UP THE PHONE AND CALL THE PERSON AT A NUMBER YOU KNOW TO VERIFY IF THEY SENT THE EMAIL OR MADE THE CALL!
Author
This article was written by Kaushal Kothari, President of Secure Guard Consulting, LLC, a cybersecurity / IT audit and consulting company. Kaushal is a former FDIC IT examination analyst and certified ethical hacker with 15+ years of experience in the technology field.
