Welcome to the fifth blog in our series of blogs discussing phishing and social engineering – and ways of protecting yourself from hackers. Today, we’ll be discussing spear phishing.
Bullet Point Summary
- Spear phishing is when a fraudulent email is sent appearing to be legitimately sent by the person (for example, an attacker sending an email to you from my email address, kkothari@sgcsecure.com). This is an example of spear phishing.
- Spear phishing is not as hard as it would seem; it’s actually very easy for a hacker to perform this type of attack.
- Understand behavior. Does the email you receive seem like it’s normal and asking for a normal request? Is it expected or unexpected? Unexpected emails asking for abnormal requests should be considered suspicious, even if they look like they are coming from the specific person.
- When in doubt, verify, either in person or by calling the person who may or may not have sent you an email.
- Hackers use emotion, as well as authority to hack. Spear phishing is an authority attack.
Recap
In our last blog, we discussed how hackers use emotion in hacking. Specifically, we discussed the concept of amygdala hijacking and how the amygdala, as the part of the brain that handles emotion, when faced with some emotional trigger, hijacks processing power from other parts of the brain, namely the critical thinking centers causing people to no longer think critically.
Spear Phishing Defined
Spear phishing is defined as the fraudulent practice of sending emails ostensibly from a known or trusted sender in order to induce targeted individuals to reveal confidential information. If my email address is kaushal@cnbc.com (it’s not :)), then simply put, it’s you getting an email from kaushal@cnbc.com. When you hover or look at the actual email address on an email that’s been spear phished, you will not be able to tell that the email did not come from that person.
Emotion versus Authority
In the past few blogs we’ve focused on emotion type attacks. Spear phishing is an authority attack. By authority, we’re saying that the email is coming from what appears to be a credible source, specifically the exact email address of the person it looks like the email was sent from. This attack is especially dangerous because of the fact that it looks so real.
Example
The current President of the United States is Donald Trump. His email address (and I actually don’t know his email address) could be dtrump@whitehouse.gov. Below is an email that I’ve sent to myself spear phishing from this email address.
Below is a screen shot showing how the email appears in my email box.

Notice how it states Donald Trumps name and looks like it’s coming from Donald Trump himself? When we open the email, and look at the actual address, there is no way to tell it hasn’t come from him himself (we don’t know what his actual address is, but if we knew, or if a hacker knew, it would state it perfectly).
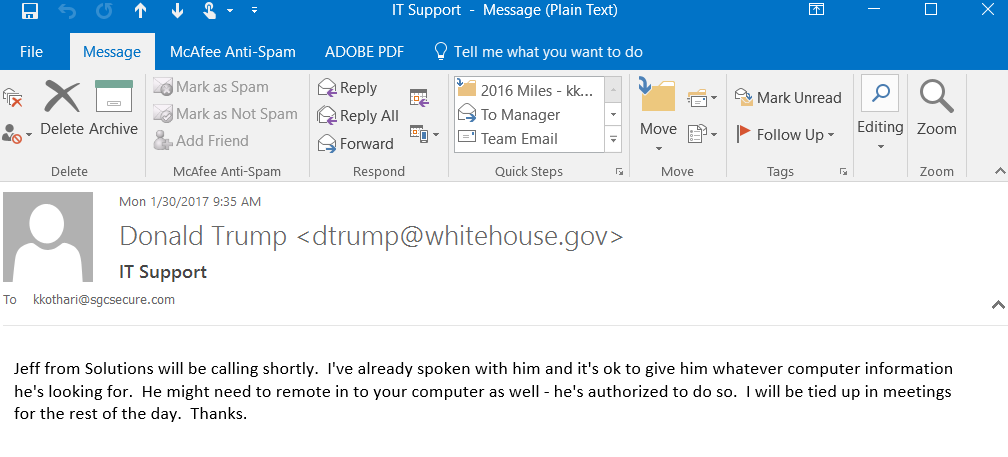
Notice how real this email looks. There’s the name, and the email address both are completely spoofed. Examining IP addresses in the message headers would give some clue regarding whether this was a legitimate email or not, but it’s a very technical solution that even more experienced IT professionals would have challenges with.
How hard is it for hackers to do this?
In terms of ease of sending a spear phishing attack, it takes under 5 lines of code and a few quick Google searches and this attack is possible. So, it’s very easy.
What can I do to protect myself?
For this type of attack, we want to keep in mind the protective controls we’ve already discussed, but to understand behavior. When an email comes through, ask yourself the question of “is this normal for the person to send me an email like this?. Also, understand if the timing is correct – if you get an email from this person on Mondays, but now this email is coming on Friday, then it’s suspicious. Look for differences in the patterns we know exist. Then simply pick up the phone and call the person, especially if the email is asking you to take some action.
Calling a person back by phone to verify if the email was legitimate is the best method of determining whether the email is legitimate. Only click on links where you not only know where the email is coming from, but the timing and nature of the email are within what you would expect.
Remember, when in doubt, call the person who sent you the email.
Wire Transfer
Over the past several years we’ve seen wire transfer instructions sent to banks by email. Banks with good sound controls in place will request those wire transfer instructions to be encrypted (to protect you) and also will do a call back by phone to the customer to ensure the wire transfer was sent.
One attack that we’ve seen performed is where a fraudulent spear phishing email is sent from an organization’s president or individual with authority to the person at the organization responsible for requesting a wire transfer from the organization’s bank. Since this was a spear phishing email, even when the bank performs a callback, the person requesting the wire transfer thinks it’s legitimate, so continues to verify the wire. What could this person have done instead? Simply call back or go and verify with the person who supposedly sent the email as to the legitimacy of the wire transfer request.
Next Blog
In our next blog, we’ll summarize what we’ve learned about phishing, and then continue on to discuss pre-text calling, a technique used by social engineers to hack by phone.
Author
This article was written by Kaushal Kothari, President of Secure Guard Consulting, LLC, a cybersecurity / IT audit and consulting company. Kaushal is a former FDIC IT examination analyst and certified ethical hacker with 15+ years of experience in the technology field.
